Cross-Border Telegram Fraud
You’re a student, or just an ordinary person trying to earn a little extra on the side. One day, you come across a message offering quick income, “Earn just by rating hotels or movies.” It sounds harmless, even tempting. You try a small task, the payment reflects instantly, and before you know it, you’re drawn deeper into what feels like a genuine side-income opportunity. But slowly, the tasks start demanding deposits, “upgrades,” and “security fees.” You convince yourself it’s temporary… until you realise you’ve been trapped in a well-crafted scam.
This is exactly how a woman ended up losing ₹16 lakh, another from Gurugram was tricked into paying ₹76 lakh, and a Mumbai man was drained of ₹1 crore all through similar “review and earn” schemes. What begins as a simple message turns into a spiral of pressure, fake promises, and financial loss.
Executive Summary This report documents a coordinated fraud scheme conducted through Telegram, involving fake Google review tasks, financial data harvesting, and an advance-fee premium plan scam. The threat actor promised payment for completing small “demo tasks,” then attempted to obtain the victim’s bank/UPI details and ultimately demanded upfront payment for “reviewer plans.”
As part of our investigation, HackElite team conducted a controlled social-engineering operation. We engaged the scammer and successfully persuaded them to click on an IP-logging link designed to capture basic network metadata, such as their approximate location.
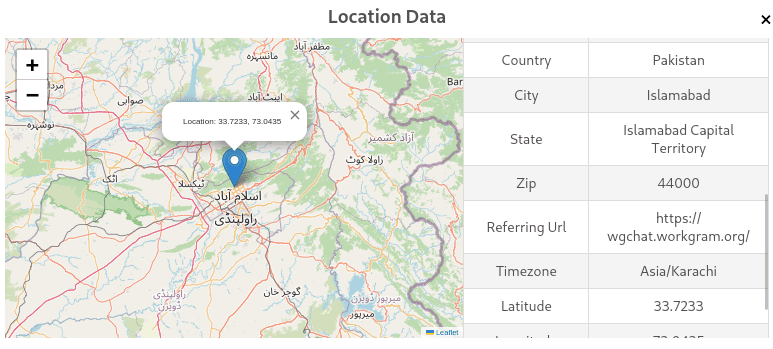
Through these steps, including the use of an IP logger, we identified that the threat actor accessed the link from Islamabad, Pakistan. The referrer URL in the IP-logger data (wgchat.workgram.org) indicates that the attacker was likely using WorkGram a cloud-based Telegram tool for bulk messaging and multi-account management, commonly exploited in large-scale spam and scam campaigns.
Background The operation follows a known pattern of fake job recruitment scams, where individuals are enticed with easy tasks like posting 5-star reviews in exchange for payment. After initial engagement, scammers:
Restrict the number of reviews a victim can perform.
Introduce paid “plans” to unlock higher earning potential.
Request banking or UPI info to commit financial fraud.
Use bulk messaging tools to reach thousands of potential victims.
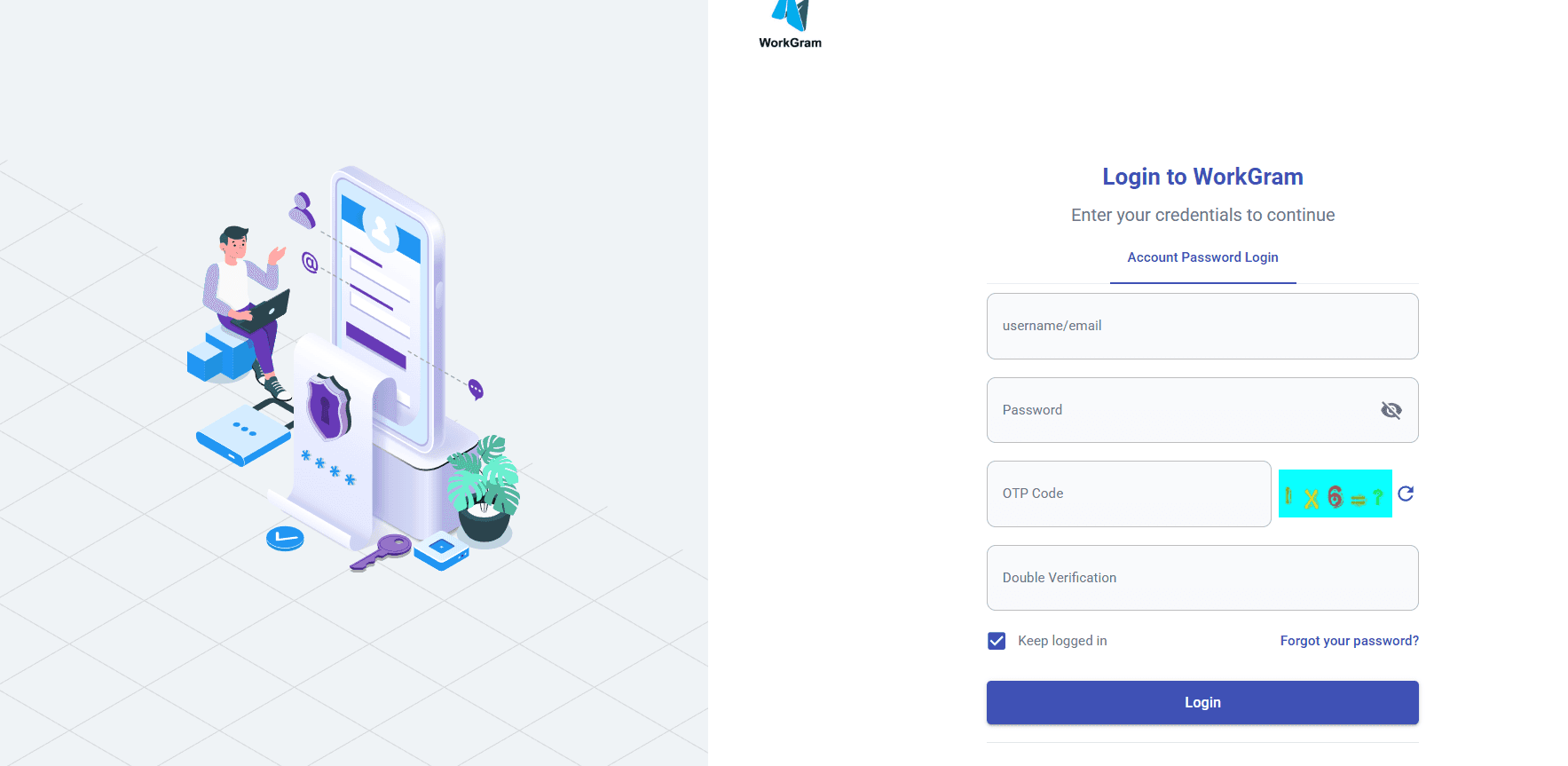
Platforms & Tools Used in the Scam During our investigation, the IP-logging results showed a referrer URL from https://wgchat.workgram.org/, which belongs to WorkGram, a cloud-based Telegram automation tool used for bulk messaging, multi-account management, and automated outreach features commonly exploited by organized scam networks.
Bulk messaging campaigns
Multi-account cloud management
Automated chat replies
Contact scraping and outreach
No need for physical SIM cards
WorkGram’s features make it ideal for wide-scale scam operations, enabling fraud networks to message thousands of Telegram users daily using automated systems.
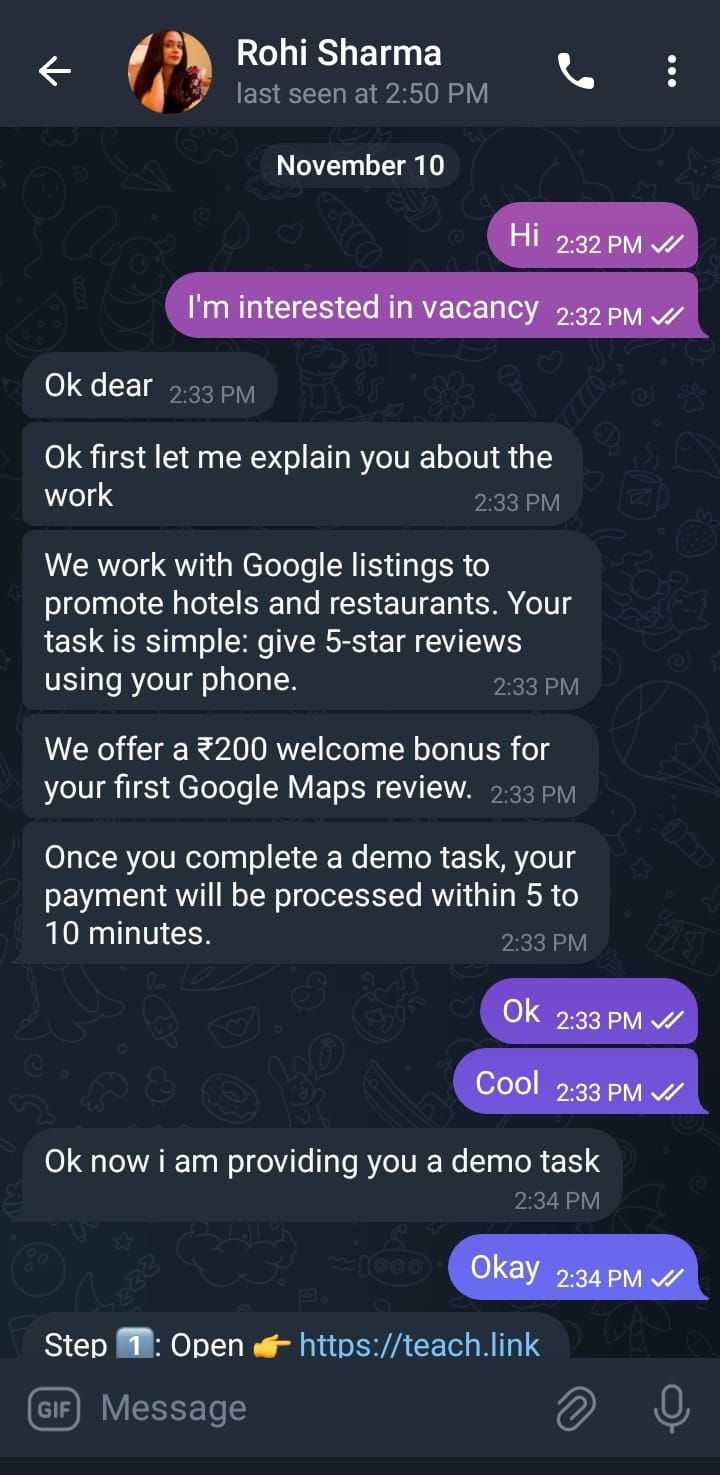
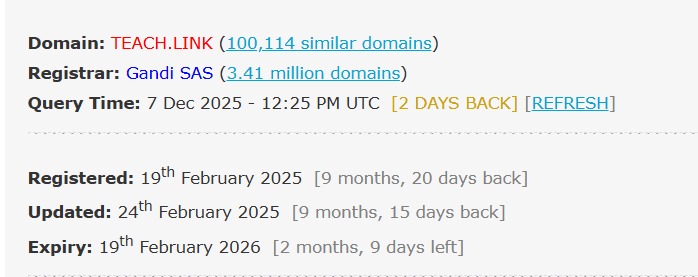
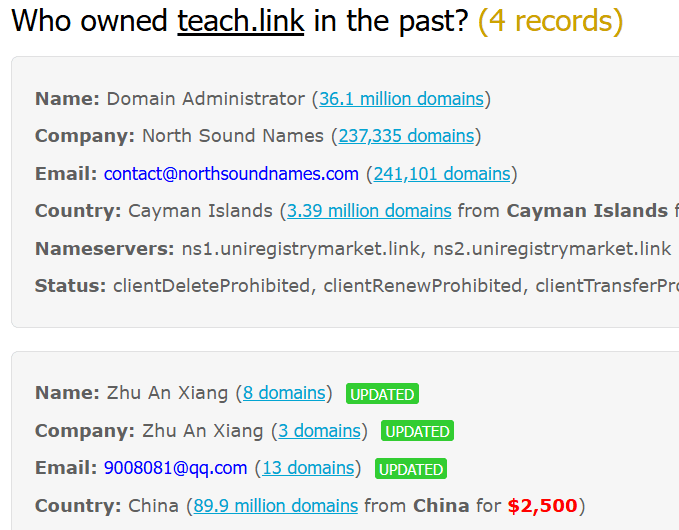
Suspicious task URL (teach.link/…) A shortened link was provided for the “demo task,” which is consistent with link-tracking and redirection commonly used by scammers. The domain teach.link, registered with Gandi SAS and expiring in February 2026, now displays fully redacted ownership information, with the only accessible historical record dating back to legacy Chinese WHOIS data from 2018 identifying Zhu An Xiang as the registrant, using the email 9008081@qq.com.
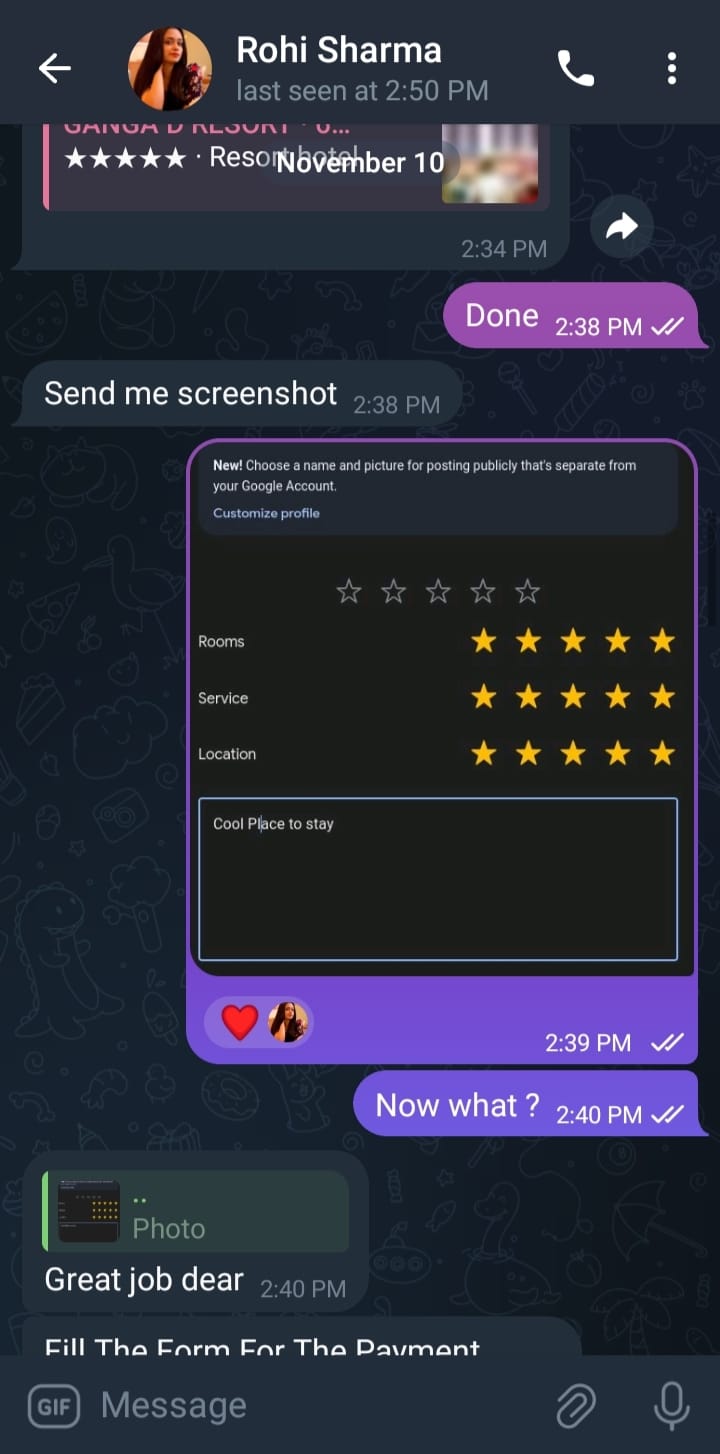
Chronology of Events The scam began when the attacker contacted the victim on Telegram under a false identity, offering paid work for completing Google Map reviews. To establish credibility, the scammer assigned a “demo task” in which the victim was instructed to perform several steps: open the provided link, select a resort, leave a 5-star review, and send a screenshot. This initial task served multiple purposes:
It confirmed the victim’s willingness to cooperate
It acted as a hook to escalate the scam
It helped the scammer build artificial trust and legitimacy
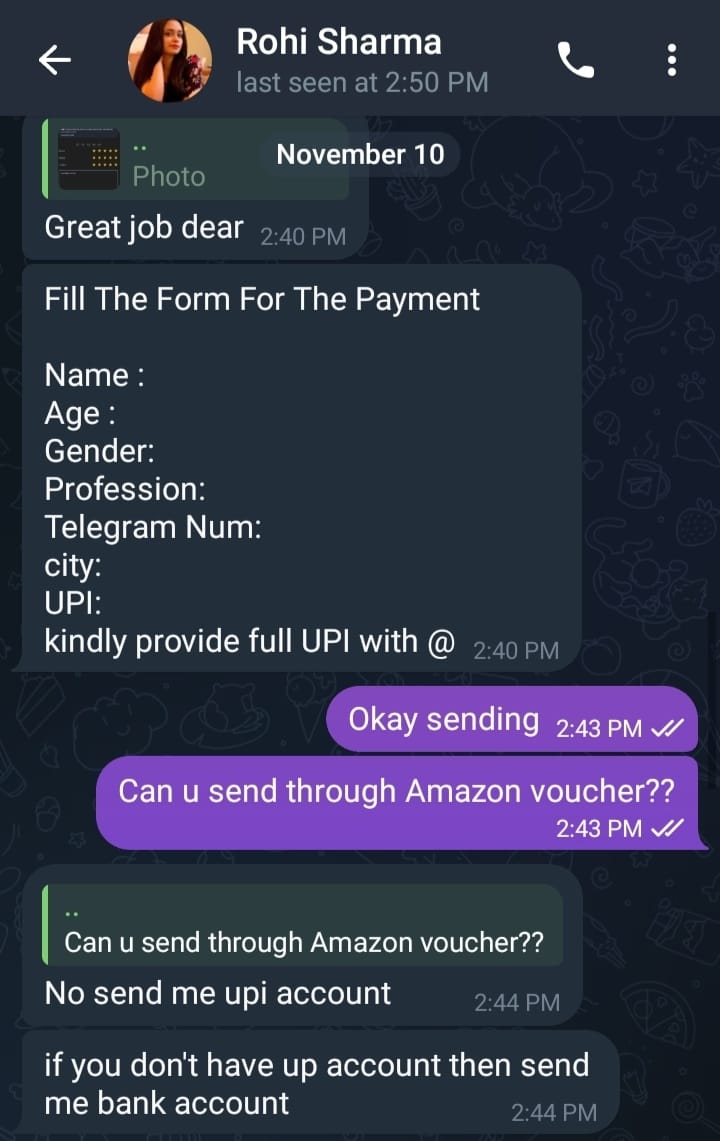
Immediate Pressure for Financial Information Once the victim sent “done,” the scammer quickly demanded:
Bank account details
UPI ID
Payment method confirmation
This is a strong indicator of financial fraud intent.
Introduction of Premium Plans (Advance-Fee Scam Stage). The scammer then introduced artificial “review limits”, “You can only review 5–6 reviews a day.”
Next, they presented paid plans:
Silver Plan – ₹5000 for 100 reviews
Gold Plan – ₹10,000 for 200 reviews
Victims who pay for these plans:
Never receive any income
Are often asked for additional fees (activation charges, taxes, verification fees)
Get blocked once they stop paying
Geolocation & IP Logger Findings
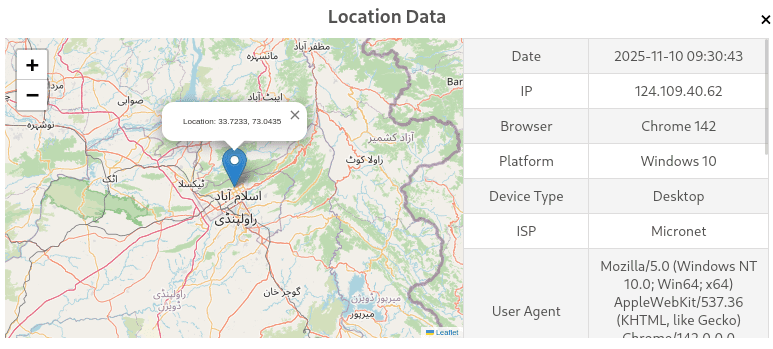
As part of our investigation, our team conducted a controlled social-engineering operation. We engaged the scammer and successfully persuaded them to click on an IP-logging link designed to capture network metadata. Once the scammer accessed the link, the logger recorded the following information:
Country: Pakistan
City: Islamabad
State: Islamabad Capital Territory
ZIP: 44000
Timezone: Asia/Karachi
Latitude: 33.7233
Longitude: 73.0435
Referrer URL: https://wgchat.workgram.org/
Browser: Chrome142
Device: Desktop/ Windows 10
Assessment of Findings
The collected data indicates:
The threat actor is operating from Pakistan, with the geolocation pointing specifically to Islamabad.
The referrer URL (wgchat.workgram.org) confirms that the actor is using WorkGram, a cloud-based Telegram bulk messaging and automation platform frequently exploited by scam networks for mass outreach.
The presence of WorkGram infrastructure strongly suggests this is an organized, large-scale scam operation, not an isolated individual.

Indicators of Compromise (IOCs)
URLs Associated with the Scam
teach.link/...
wgchat.workgram.org (bulk messaging dashboard used by scammer)
Behavioural Indicators
Asking for UPI/bank details
Selling job “plans”
Offering unrealistic payouts
Urgency and high-pressure messaging
Telegram-based communication only
Grammar inconsistencies common in scam scripts
Recommended Actions
For the Victim
Immediately block and report the Telegram account
Do NOT send any money or financial details
If any banking info was shared, contact the bank fraud department
Enable Telegram 2FA
Avoid any future contact
Reporting
Submit this report and screenshots to:
National Cybercrime Portal (call the national toll-free helpline 1930 or visit https://cybercrime.gov.in/)
Telegram Fraud Reporting