Fake e-Challan Phishing Scam
Analysis of a Fake e-Challan Phishing Scam Targeting Indian Citizens
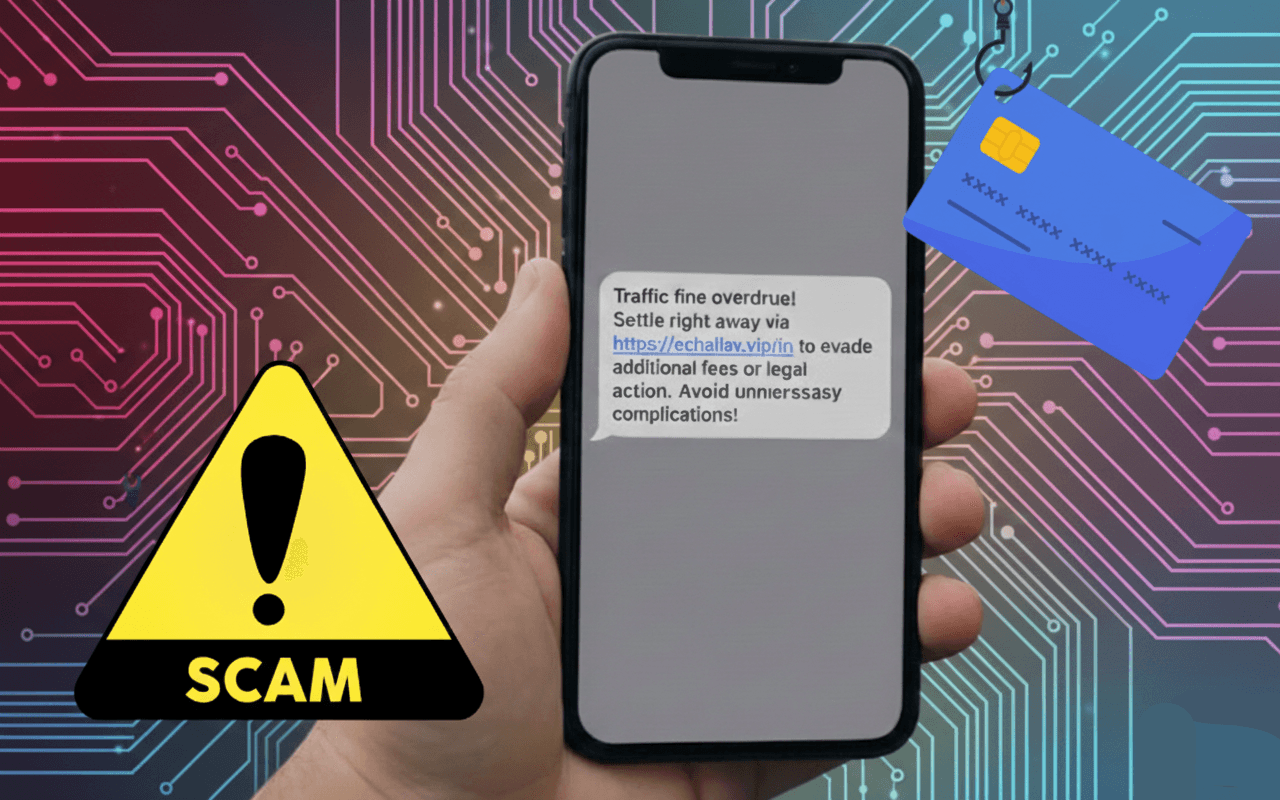
With the increasing adoption of digital governance in India, services such as e-Challan have simplified traffic fine management for citizens. However, cybercriminals are actively exploiting public trust in these systems by creating fraudulent messages and phishing websites that impersonate official government platforms. This report documents a fake e-Challan phishing scam observed through SMS and WhatsApp messages, which redirect users to a malicious website designed to steal debit/credit card details. The objective of this report is to explain how the scam operates, identify red flags, and raise awareness so that users can protect themselves and help prevent further victimization.
Scam Overview
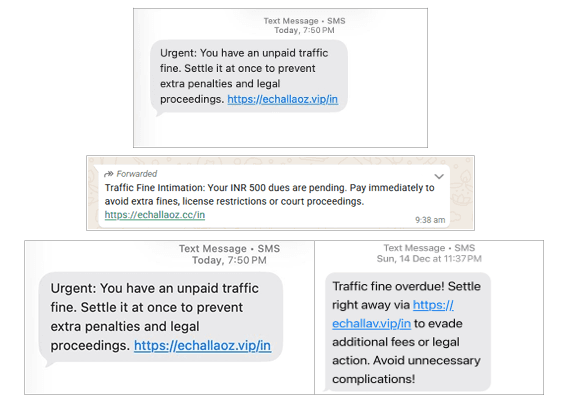
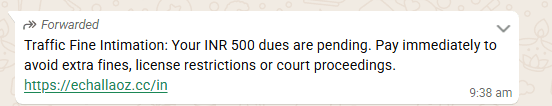
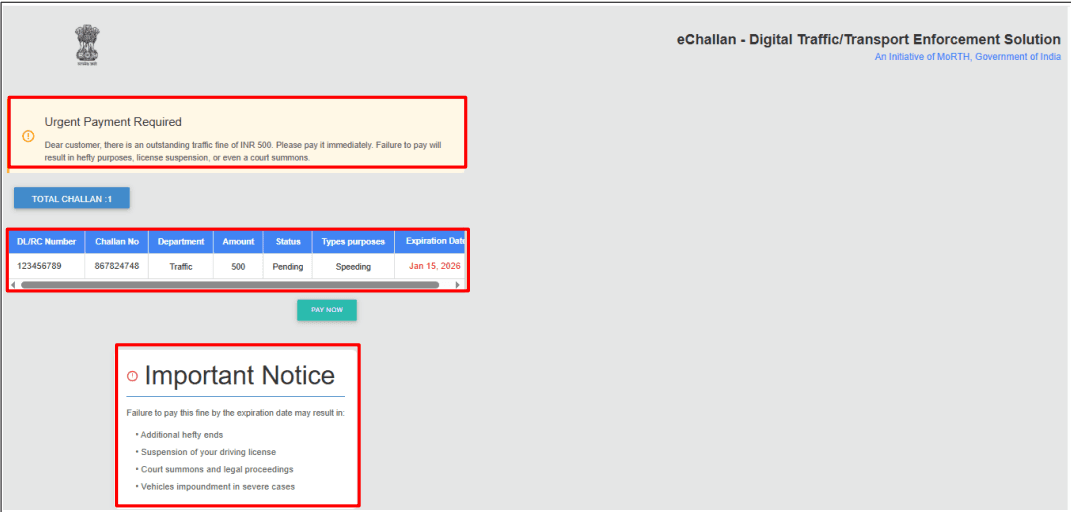
The scam begins with users receiving alarming messages claiming that a traffic fine of INR 500 is overdue and must be paid immediately to avoid legal action, license suspension, or additional penalties
Observed Message Characteristics:
• Urgent language such as “Pay immediately”, “Avoid legal action”
• A suspicious web link resembling the official e-Challan portal
• Sender appears as a random mobile number, not a verified government short code
• No specific challan details (date, location, vehicle number)
Example domains observed:
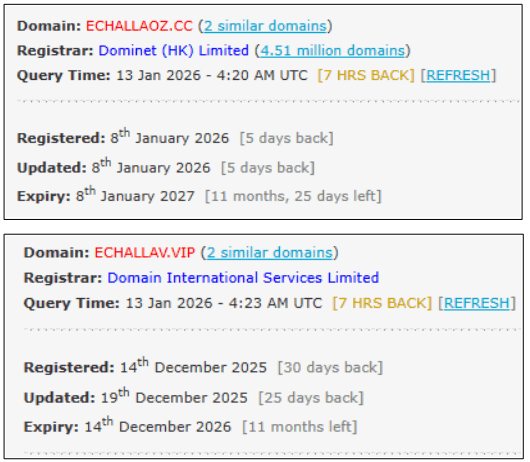
• echallaoz.cc/in
These domains are not official Government of India domains. So when these domains was registered, From website registration record it was observed that these websites are very recently predigested.
Analysis of Associated Infrastructure Using CTI Tool
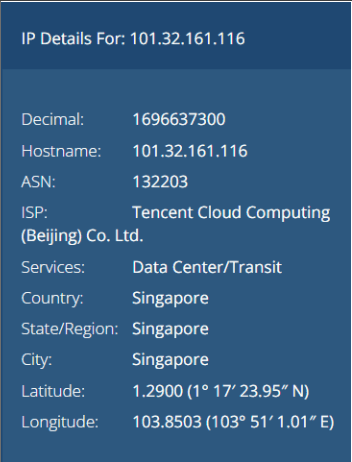
With the help of our Cyber Threat Intelligence (CTI) tool, we identified multiple similarlooking domains associated with the same phishing campaign, even though they are registered with different registrars. Analysis further shows that 101.32.161.116 is the server IP address, and these related domains are hosted on the same server, indicating shared infrastructure and a coordinated phishing operation.
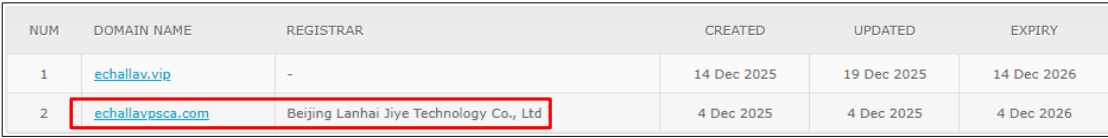
The domain (echallavpsa.com) was registered through Beijing Lanhai Jiye Technology Co., Ltd (Chinese: 北京蓝海基业科技有限公司), a China-based ICANN-accredited domain name registrar.
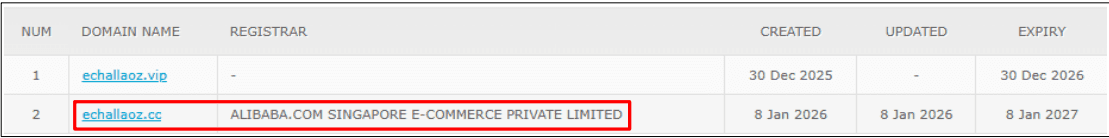
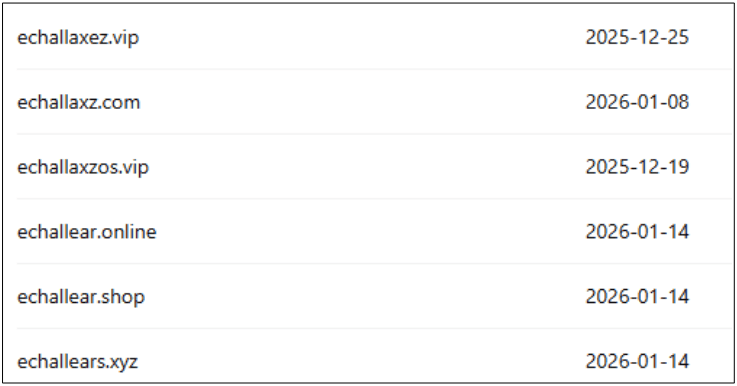
The presence of multiple similarly named domains such as echallavpsca.com and echallaoz.cc strongly indicates a coordinated and long-running phishing campaign rather than a one-off attempt. Registering several look-alike domains allows the attackers to quickly rotate infrastructure, evade takedowns, and continue operations seamlessly. This pattern suggests a clear intent to scale the attack and target a larger number of victims over time.
Details related to IP Address 101.32.161.116
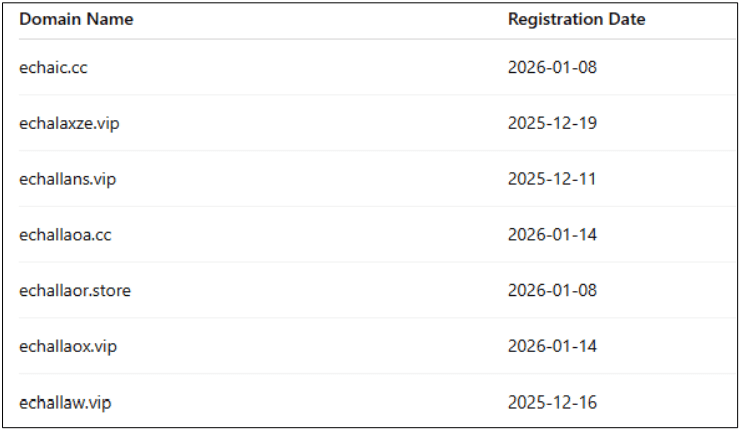
Similar Domain are mentioned below:
Technical Analysis: How the Scam Works
Step 1: Phishing Message Delivery
• Messages are sent via SMS or WhatsApp using random Indian mobile numbers.
• Attackers rely on fear and urgency to force quick action.
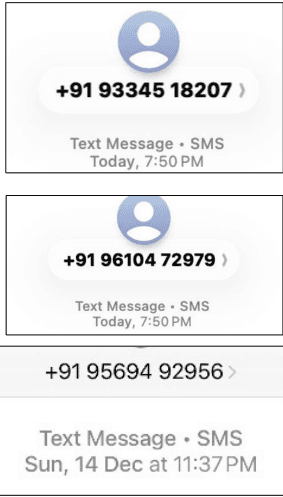
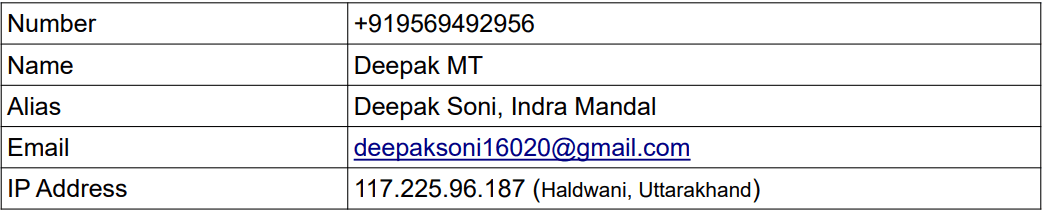
Analysis of Sender Phone Number (+919569492956) Using In-House tool .
One of the mobile numbers used to distribute the phishing e-Challan link was analyzed using our in-house threat intelligence and reconnaissance tool. The tool was able to correlate this number with multiple metadata indicators, helping establish its involvement in fraudulent activity. The analysis focused on telecom-level information, behavioral patterns, and risk indicators commonly associated with phishing and scam campaigns. While no legitimate government association was found, the collected intelligence strongly suggests misuse of the number for social engineering and cyber fraud operations.
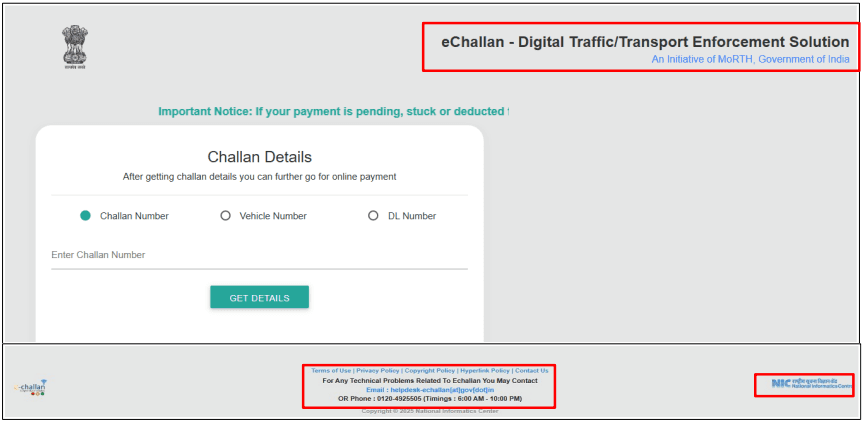
Step 2: Fake Government Website
• The link opens a look-alike website mimicking the official e-Challan portal.
• Government logos and titles like “An Initiative of MoRTH, Government of India” are used to appear legitimate..
Step 3: Fake Challan Validation
• The website allows users to enter any challan number.
• Regardless of the input, the site always shows a fine of INR 500, confirming that:
• No backend validation exists
• This is a static, scripted response
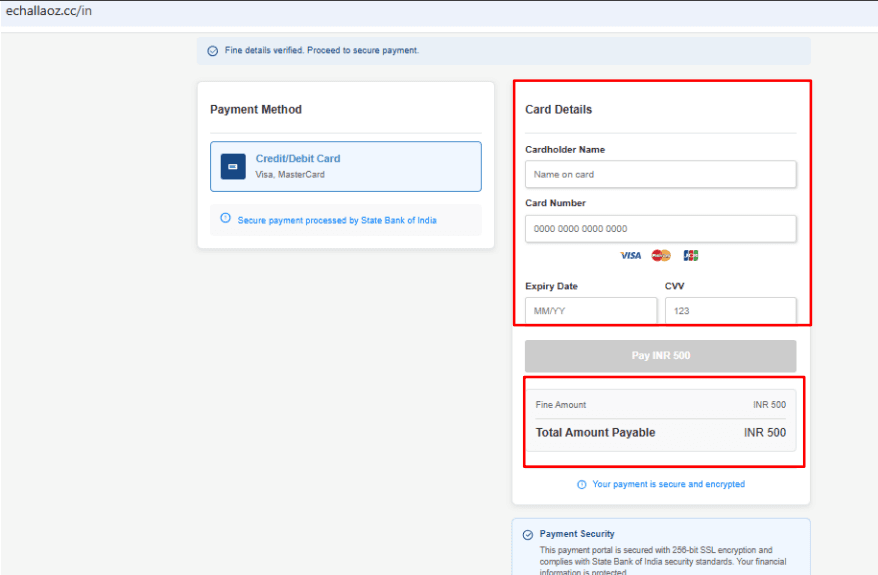
Step 4: Payment Page (Critical Risk)
• The site asks for full credit/debit card details, including:
• Card number
• Expiry date
• CVV
• This is a major red flag, as legitimate Indian government portals:
• Redirect to secure payment gateways
• Never directly collect CVV details on their own page
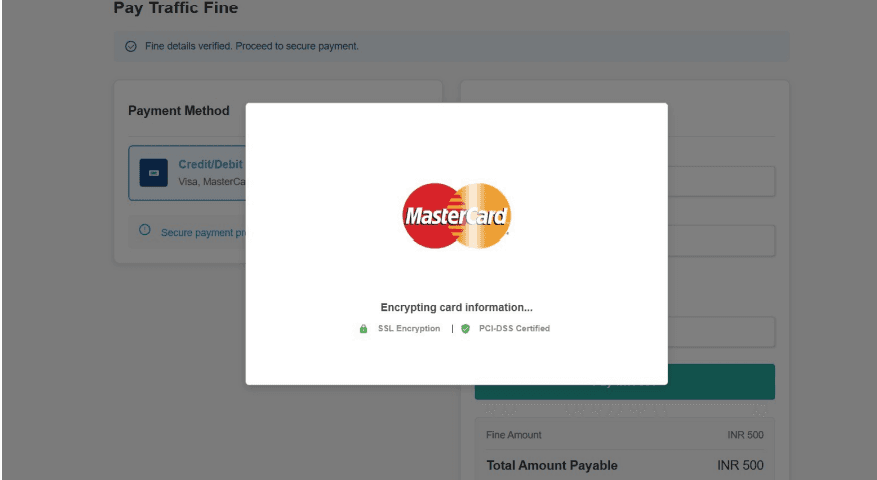
Fake processing Screen: This screen is designed to falsely reassure users by displaying well-known card network logos and security claims such as “SSL Encryption” and “PCI-DSS Certified.” In reality, this is not a legitimate payment gateway. No verified bank or government payment processor displays card-brand logos in this manner while directly collecting full card details, including CVV. The “encrypting card information” message is purely visual and serves as a social engineering tactic to gain user trust while sensitive financial data is being captured by attackers.
Step 5: Data Harvesting and Fraud
• Entered card details are likely:
• Stored by attackers
• Used for unauthorized transactions
• Sold on dark web marketplaces
• Victims may experience financial loss hours or days later, making tracing difficult.
4. Key Red Flags Identified
1. Unofficial domain names (not ending in .gov.in)
2. Same fine amount shown for all challan numbers
3. Direct card detail collection including CVV
4. Urgent and threatening language
5. No vehicle number, violation date, or location mentioned
6. Payment not routed through trusted gateways (UPI, SBIePay, etc.)
5. Impact and Risk Assessment
• High risk of financial fraud Possible identity theft
• Targets both tech-savvy and non-technical users
• Can spread rapidly through forwarded messages
• Damages public trust in genuine digital governance platforms
6. Recommended Actions
For Individuals
• Do not click on suspicious links received via SMS/WhatsApp
• Never enter card details on unknown websites
• Verify challans only through official portal: https://echallan.parivahan.gov.in
• If card details were entered:
• Immediately block the card
• Inform the bank
• Monitor transactions closely
For Reporting the Scam
• Report phishing websites to:
• Indian Cyber Crime Portal: https://cybercrime.gov.in
• Share details with:
• Local cyber cell
• Bank fraud department
• Forward suspicious SMS to 1909 (India’s spam reporting service)
7. Conclusion
This fake e-Challan scam is a well-designed phishing attack leveraging public trust in government digital services. By imitating official portals and exploiting urgency, attackers successfully trick users into revealing sensitive financial information
Public awareness, timely reporting, and basic cyber hygiene are critical in preventing such scams. Citizens must remain vigilant and verify all payment requests through official government channels only.